I have reviewed Microsoft?s Enhanced Mitigation Experience Toolkit a few days ago here on Ghacks and have found it to be an excellent security program. The software basically mitigates several popular exploitation techniques, making it an effective last line of defense tool when a PC running Windows is attacked with vulnerabilities that are not known or at least not fixed yet.
What makes EMET special is not only the program?s mitigation techniques, but also that it ships with an easy to use program interface. Even inexperienced users can use the program to add extra protection to their system, and while they sometimes may run into issues, it is nothing that can?t be easily fixed with a few clicks of the mouse button.
Today, Microsoft is making available a technology preview version of EMET 3.5 which incorporates a new exploit mitigation technique that mitigates Return Oriented Programming (ROP) attacks. The following definition has been taken from Wikipedia.
Return-oriented programming (also called ?chunk-borrowing ? la Krahmer?) is a computer security exploit technique in which the attacker uses control of the call stack to indirectly execute cherry-picked machine instructions or groups of machine instructions immediately prior to the return instruction in subroutines within the existing program code, in a way similar to the execution of a threaded code interpreter.
Because all the instructions that are executed are from executable memory areas within the original program, this avoids the need for direct code injection, and circumvents most measures that try to prevent the execution of instructions from user-controlled memory.
The technology that Microsoft has implemented into the technology preview was submitted by one of the contestants of the company?s BlueHat Price challenge. The EMET team added four checks into the program to help prevent attacks using ROP techniques.
Installation and use
The Enhanced Mitigation Experience Toolkit 3.5 Tech Preview can not be installed on systems that run other versions of EMET. A prompt is displayed on those systems that is informing users that the current version needs to be uninstalled before the tech preview can be installed. Since it is a tech preview, it is not recommended to install it in a productive work environment. It is also recommended to export the current configuration using the file menu for backup purposes.
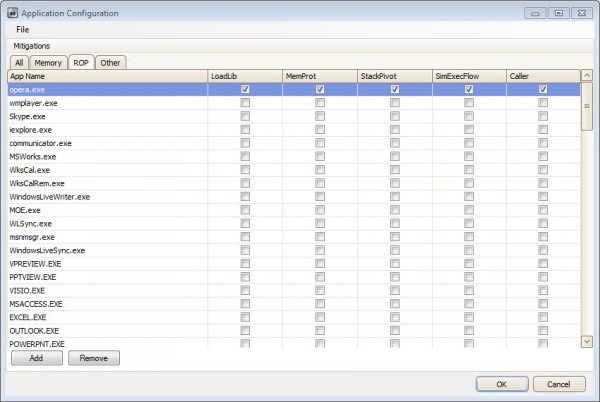
When you start EMET 3.5 for the first time you will notice that Microsoft has added tabs to the application configuration window. You can still display all mitigation techniques in a single tab, or use the memory, ROP or other tab to configure specific features.
Closing Words
Microsoft seems very dedicated when it comes to EMET and it may only be a question of time before the program gets integrated into the Windows operating system in one way or the other. For now though, Windows users need to download, run and configure it separately. Should they? Yes, definitely.
EMET, Microsoft?s Enhanced Mitigation Experience ToolkituTorrent 1.6.1 update fixes remote exploit
Update Windows without Microsoft
Microsoft Sees Huge Increase In Java Exploit Attempts, Surpassing Adobe
Update Microsoft Security Essentials On Computers Without Internet
Enjoyed the article?: Then sign-up for our free newsletter or RSS feed to kick off your day with the latest technology news and tips, or share the article with your friends and contacts on Facebook, Twitter or Google+ using the icons below.
About the Author:Martin Brinkmann is a journalist from Germany who founded Ghacks Technology News Back in 2005. He is passionate about all things tech and knows the Internet and computers like the back of his hand. You can follow Martin on Facebook or Twitter.You are here: Home ? Security ? Microsoft EMET update with new exploit mitigation technology
Next Post:
Click on the following link(s) to read more about Security, Windows
Source: http://www.ghacks.net/2012/07/25/microsoft-emet-update-with-new-exploit-mitigation-technology/
manson bubba watson recent earthquakes lollapalooza fbi most wanted list stuttering james van der beek
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.